Hardened distroless
containers with a
distro experience.
Koala’s Hardened “out-of-the-box” containers enable
continuous compliance & reduce CVE sprawl.


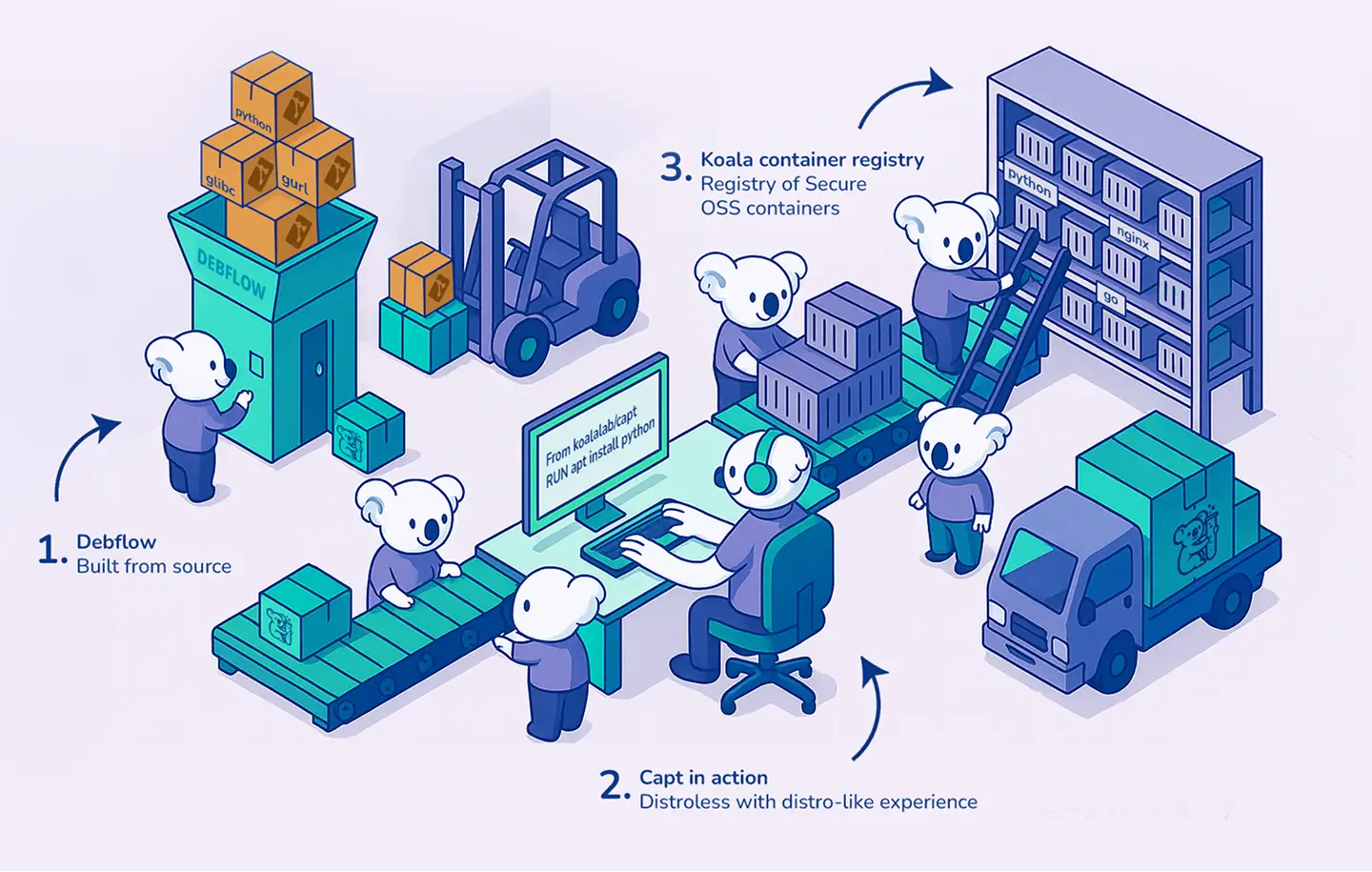
0-Deb: Our container-first linux distro
for hardened containers.

0-deb: Linux for Hardened Containers

apt-based workflows with distroless security

Further hardening before enterprise release

Secure Software. Unlock Revenue.
Build your application on Koala's hardened base container images and give your developers a familiar linux experience.
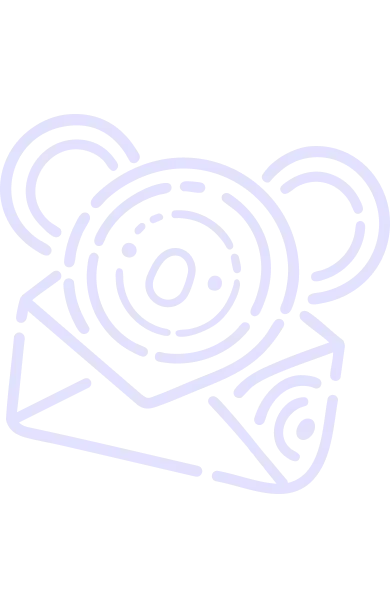
88% less CVE accumulation
Ensure continuous compliance

Remove 90% of your CVEs
Securely manage the tech sprawl
95% less High+Critical CVEs
Ensure no release blockers

Faster builds, faster boot time
Containers your cloud team will love
Accelerate your compliance.
Koala base container images enable continuous compliance across the increasing vulnerability management standards of FedRAMP, PCI, CRA compliances
Unlock team productivity.
Unlock productivity for your security teams. With 90% less CVEs in your applications, koala container images reduce CVE patching & management overhead.

Developers love this.
Koala's debloated containers ensure rare release blockers, familiar toolchain and efficient cloud infra; your developers will love these containers.


Rethinking the Linux distro from a container-first perspective
Traditional Linux distributions carry assumptions incompatible with container deployment. Learn how 0-deb reimagines package management for ephemeral, immutable environments.
- .Debflow — Reproducible builds with multi-source vulnerability tracking
- .Captain — Zero-footprint package manager for container builds
- .Security Pipeline — Automated CVE discovery and patching
What industry leaders are saying..
Ask, plug in, collaborate
Let us know how we can help you reduce CVEs, meet compliance, and ship safer code.